
I’ve always been mesmerized by the digital world and the endless possibilities it offers to connect. However, with every new innovation comes a new set of threats. And, this is right where the critical role of the Security Operations Center (SOC) comes in to protect organizations from cyberattacks.
In fact, this role is becoming so critical that a staggering 70% of organizations now consider their SOC to be very important for their overall security strategy. (Source: Ponemon Institute survey)
So, as a SOC analyst myself, I’m on the front line of the digital background, protecting organizations from cyber threats. And, in this read, I’ll be sharing my personal insights into the key role of SOC analysts in today’s interconnected world.
Let’s start!
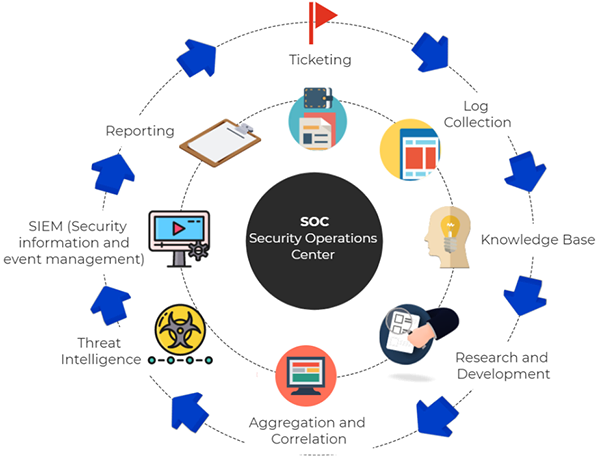
As a SOC by profession, I usually work on teams to monitor, analyze, and respond to security issues. My day-to-day involves a dynamic mix of technical skills, which involves monitoring a network to detect any signs of threats and respond to them immediately before they can cause significant damage to the organization.
So, from analyzing the network traffic to hunting down advanced threats, we employ a range of tools and techniques to make sure that there’s no suspicious activity happening.
In addition to that, SOC analysts also work with other departments of the company, such as human resources or sales, to ensure their systems are secure. Also, if someone from any of those departments faces any issue with their work computer, this also will be their duty to fix it.
One of your primary goals is to detect threats in cybersecurity operations in their initial stage before they can cause any further harm. We also leverage a variety of powerful tools, such as SIEM (Security Information and Event Management), to identify patterns of any potential threats. Beyond individual analyst efforts, many organizations opt for comprehensive, managed solutions to ensure these critical functions are consistently performed. Such services provide 24/7 monitoring and leverage advanced analytics to detect even the most subtle indicators of compromise. This proactive approach ensures that potential threats are not only identified quickly but also thoroughly investigated and neutralized before they can escalate. For businesses seeking robust, continuous protection, a dedicated soc security service offers the specialized expertise and infrastructure needed to maintain a resilient security posture.
When a cyber incident occurs, it’s crucial to respond quickly to minimize the damage. And as a SOC analyst, we’re often tasked to investigate the root cause of the incidents to prevent any future occurrence and develop a comprehensive response plan.
To safeguard our network, we’re required to monitor our system in real time. This involves analyzing the network traffic to detect any suspicious activity in the system.
Do You Know?
According to the Ponemon/Devo study, 50% of the organizations rate their SOC as being highly effective in resolving any security incident.
No doubt that a data breach can have a devastating impact on the organization, both financially and reputationally. And, this is where we implement a layered security approach such as strong access control and encryption to prevent this loss.
Other than that, we also stay updated on the latest best cybersecurity practices and industry standards to always stay ahead of the cyber bullies.
Do you know what the primary cause of data breach is? It’s human error! And, this is why we often conduct some security awareness training sessions and simulations so that employees can recognise and report any threat they encounter.
As cyberbullies are often coming up with new ways to exploit the system. This is our duty to conduct regular risk assessments and vulnerability scans to mitigate cyber risks in our security infrastructure.
A cyber system control center plays a pivotal role in protecting sensitive data. We also use some fine techniques like firewalls, intrusion detection systems, and network segmentation to ensure network security.
Do You Know?
According to Security magazine, about 90% of SOC analysts believe that the current threat detection tools are effective in safeguarding the digital interests of an organization.
As the digital world is constantly evolving, so do cyber threats. And one of our prime responsibilities as an organization is to continuously update our knowledge and stay informed about the latest security trends.
Simply by combining all of our technical expertise and working closely with other teams, we ensure to build a resilient security posture that can repel even the most sophisticated attacks.
In closing, as a SOC analyst, I’ve firsthand witnessed the critical role we play in an organization to safeguard its network system. From monitoring the system for any potential threat to planning a comprehensive response during a cyber incident, we ensure to defend the digital assets of an organization, while setting up a secure future.
Subscribe to our newsletter and get top Tech, Gaming & Streaming latest news, updates and amazing offers delivered directly in your inbox.