
As a business owner, confidentiality is my priority, but do you know what else is? It’s the interior protection which I don’t mess with. I’ve seen companies making mistakes in this field, but what is physical security?
According to a case study, “Physical integrity refers to the measures and mechanisms implemented to safeguard physical assets, such as buildings, equipment, and personnel, from unauthorized access, theft, vandalism, or damage”(ResearchGate: Physical Security to Cybersecurity).
In this article, I will tell you how you can strengthen your cyber and physical security to protect your organization. It’s an important write-up, so pay attention.
Cybersecurity protects you from all those threats that can attack from outside without being present physically. They can breach to steal data or do harm in other ways. It’s mostly done by hackers and malware.
But physical security protects you from those who come undercover in your company for some alternate motive like getting a restricted document or gaining entry to files. These are done by real people who are present at the moment and might be standing next to you right now.
Companies need to take care of both issues as both can result in great damage that can cause harm to your businesses. Both of these issues need equal attention and proper measures need to be taken.

Every company has that one restricted area that is not accessible to only one. Such places contain sensitive information and very few people have exposure to it. But Outsiders can try to break in, so what should you do?
Consider installing an alarm monitoring system, so in case anyone tries anything fishy, safety staff will be alerted immediately. Such systems usually consist of CCTV, intrusion detection, and access control systems.
This is a must to have in all organizations if they want to secure their most important data. You’ll be able to detect threats easily and take immediate action if anything happens.
Technology has advanced a lot in the past decade, and it has only worked in our favor. For example, you can install IoT-embedded motion sensors, and cameras and have the right to real-time data from anywhere.
AI can also be incorporated easily and be used to analyze different data to make future predictions. Based on the insights, you can take different routes to eliminate any risk that might surface.
But you have to be careful as IoT-based devices can become the victim of cyberattacks, this is why you’ll need a good encryption source so no one can damage your devices.
Just installing all the devices isn’t enough. Your job has only started. You have to monitor both cyber and physical perimeters, as the danger can come from anywhere. If there’s even a bit of disturbance, you have to take immediate action.
Real-time tracking can be done with centralized dashboards combined with physical alarms and wireless controls. Another very effective step is a triggering system so in case any unauthorized activity is detected the system will shut down or all your important data will be locked temporarily.
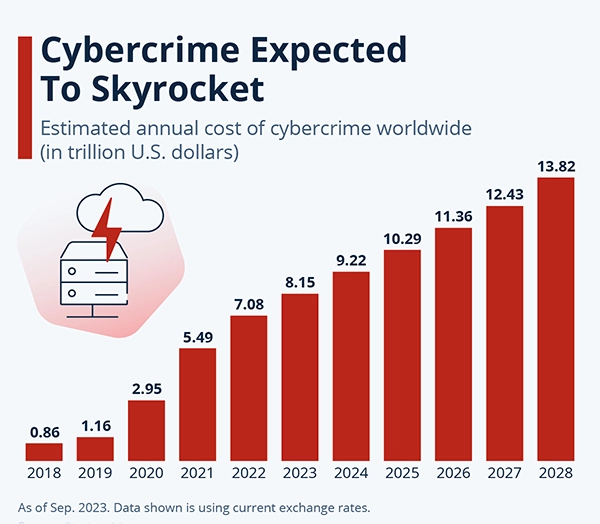
Look, cybercrime is expected to skyrocket because hackers and malware keep coming up with new tactics. You have to be prepared as well.
From my experience, I can tell you that even the strongest system fails because if the employees are not trained well.
Staff members must be taught about suspicious activity, recognize phishing, how to manage their access, etc. It’s an important step, and organizations can conduct seminars specially for this so it could reach everyone.
An integrated defense strategy is crucial as you have to take care of your virtual and physical privacy, so you need a coordinated solution that will complement both. Think about all the possible risks and see all angles so you don’t miss out on anything.
Conducting audits, timely maintenance, and software upgrades are essential. You have to keep tabs on all the weak points and think of a solution to get past them.
FUN FACT
The first cyber theft took place in 1834 when two hackers stole financial market information by getting into the French Telegraph System!

Threats are evolving rapidly, but that doesn’t mean the tools to fight them aren’t. New trends like blockchain, biometrics, and AI-driven analytics are helping in the creation of stronger networks that wouldn’t be easy to bypass.
Organizations have to work on their adoption process. New technologies will keep on coming, and how they’ll be incorporated and what strategies will be made with them will be the ultimate key to protection.
So, these are just some of the ways that I could tell you how you can increase your cyber and physical security. There are many more ways, but these are inflexible. Make sure that you apply them for a better network.
Subscribe to our newsletter and get top Tech, Gaming & Streaming latest news, updates and amazing offers delivered directly in your inbox.