
At a time when technical advancements never fail to amaze us, the prevention of ‘cyber breaches’ and the protection of personally identifiable information is a key focus of many organizations and businesses today.
Even though multiple companies have implemented variants of safety measures, unfortunately, the traditional tactics are no longer effective in today’s advanced cyber threats.
And that’s where Cyber Asset Attack Surface Management (CAASM) comes in as your life-saver.
A software that primarily focuses on enabling security teams to overcome asset visibility and exposure challenges.
Be it business leaders, digital asset securities, and vulnerabilities, the understanding of Cyber asset attack surface management (CAASM), and how it influences the overall posture of the cybersecurity of the company is pivotal.
As you go through this article, you will know how organizations can be better protected against an increased number of cyber asset attacks by implementing CAASM.
CAASM is no less than a pair of X-ray glasses for your digital infrastructure.
Where traditional security measures often miss out on the specified security threats, this service scrolls even on hidden corners and helps you identify the security weaknesses your company might be facing.
However, the features of this amazing service don’t end here, as along with detecting the flaws, it also either fixes the problems by itself or will help you develop the strategies to improve the security rate as per the need.
According to the Source Norton Antivirus,
Over 75% of targeted cyberattacks start with an email in 2024, making phishing a primary vector for cybercrime.
CAASM – this robust tool is also designed to assist enterprises in recognizing and rectifying vulnerable areas in their digital assets’ infrastructure.
Due to its ability to continuously monitor every attack surface, it is possible to detect flaws in your systems.
These flaws may be a result of the absence of patches on the system, poorly configured services, and other weaknesses.
The service also allows you to make a ranking of vulnerabilities depending on their level of risk and potential damage caused, thus, giving you a chance to deal with the most dangerous risk first.
To summarize, a CAASM is a guard who watches over the cyberspace of an organization and helps it take precautions that lower the chances of data breaches.
Shadow IT – the term refers to the sanctioned use of software, hardware, or other systems and services within an organization, and this often does not come in the knowledge of the IT department.
And of course, if such tech is not approved by the IT consulting firms, this can surely pose a risk to the security of the organization as they are not properly managed, patched, or protected.
In such an instance, CAASM comes forward to assist the companies in detecting and managing the Shadow IT software and hardware.
It allows enterprises to identify the systems that are in use without the approval of the IT Department.
Then, it assesses the potential security risks that might be associated with those Shadow IT systems.
At last, they have been provided with effective strategies to terminate the non-approved systems.
Legacy Systems – Although this outdated software or hardware is no longer state-of-the-art, it is still in use by multiple companies and is often targeted by security threats due to lack of maintenance.
In this case, CAASM works similarly as it did when managing the Shadow IT i.e. detecting the system that is no longer supported, analyzing the amount of risks, and how the cybersecurity consulting services can handle it.
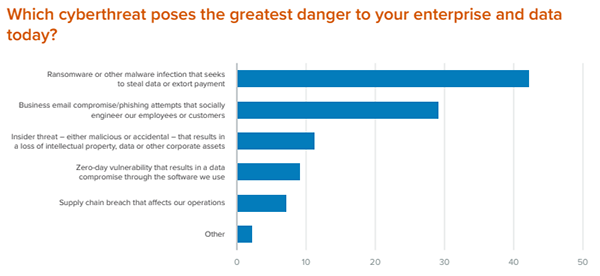
Cyber Asset Attack Surface Management (CAASM) can now make an active role in improving your security operations by working alongside your current security tools.
That’s how it even saves the time and effort of the security team.
The service incorporates information from SIEM, EDR, and vulnerability management platforms to make it possible for it to consolidate a view of risk exposure in a unified design which makes it easy to effectively respond to an incident, and address concerns priority.
Indeed, it will still take so many more years to completely vanish the complex landscape of cyber threats.
And until then, only the incorporation of tech life-saver tools such as CAASM can be your only resource in safeguarding your organization’s digital assets.
With its offering to view all cyber assets and attack surfaces, it allows the security team of your company to proactively address vulnerabilities, and respond to the incident immediately.
As multiple companies are continually adopting cloud services, IoT, and remote work setups, it’s become even more vital to instantly incorporate the service of CAASM, and secure and manage the attack surface efficiently.
Subscribe to our newsletter and get top Tech, Gaming & Streaming latest news, updates and amazing offers delivered directly in your inbox.