
“Threat intelligence is not about finding the silver bullet that will stop all attacks. It’s about making informed decisions to better mitigate risk.”
— Graham Cluley (Cybersecurity Expert)
It is hidden from none that cyberattacks are not a rare occurrence these days. Not only more prevalent, but with advanced technology, they are stronger and costlier than ever. The worldwide expense of data breaches has reached $4.45 million in 2023, showing a 15% rise from 2020. (Forbes: Cyber Threats and the Growing Complexity of Cybersecurity)
To safeguard my organization from such attacks, I leverage some tools and techniques for threat intelligence analysis. This proactive approach keeps us covered against potential risks and shields us from any cyber adversary.
Want to know about these effective solutions? Stay tuned till the end and uncover these key components.
You can understand threat intelligence as a security system that gathers relevant information from various sources, analyzes and categorizes it, and then utilizes the insights gained to improve the organization’s security posture.
This proactive approach keeps us ahead of potential attackers through continuous collection and processing of the data, empowering us to defend against known as well as emerging threats.
Everyone knows that cyber-attacks these days are not like they used to be, hence can’t be tackled with those old, traditional methods. Now cyber criminals use sophisticated tactics, techniques, and procedures (TTPs) that are far more difficult to deal with.
Think of it like this, to save yourself from such highly advanced attacks, you need to keep your walls up at all times, on the other hand, the threat actor only needs one small opening or opportunity to pass through your security system. That means the attacker is calling the shots in such situations.
Therefore, you need a savvy security system to outsmart the attacker. Threat intelligence analysis provides you with exactly that and protects your organization from malicious attacks.
FUN FACT
On average, there are 2,244 cyberattacks per day or around 93 attacks per hour. That’s more than one attack every minute!
Now that I have discussed the role and impact of threat intelligence analysis on businesses, I think it will be best if I share some effective techniques. So, the four tactics that I find the most advantageous are as follows –
Another integral component that dictates the effectiveness of your system is the tools you use for threat intelligence analysis. Here are some effectual tools that are used widely in my organization.
I have suggested some effective tools and techniques, but how to integrate them into your business and build an effective threat intelligence program? In this segment, I’ll walk you through all the necessary steps for creating the program.
Albeit the benefits threat intelligence analysis provides, it comes with various challenges. Here are some issues I came across in the implementation and how I overcame them.
Looking at the current landscape, it can be said that threat intelligence is rapidly evolving and in the future, we can expect the integration of advanced technologies like artificial intelligence and machine learning for better analysis of data and threat hunting.
Unlike traditional threat intelligence, future trends will shift the focus more toward behavioral analytics and contextual threat intelligence.
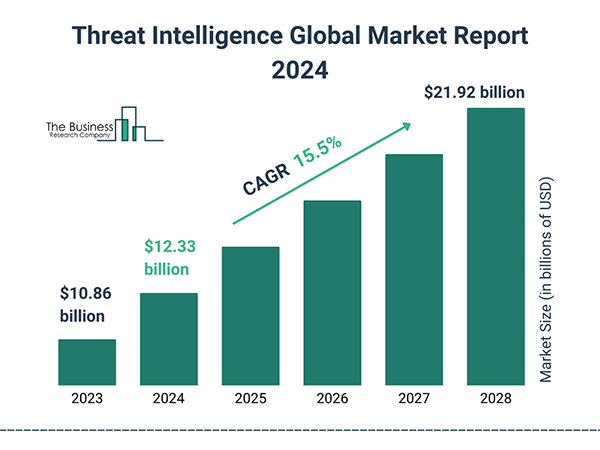
Talking about its market size, the threat intelligence market is expected to rise from $12.33 billion in 2024 to $21.92 billion in 2028, growing with a CAGR of 15.5%.
In this article, we discussed how threat intelligence analysis helps organizations anticipate, detect, and mitigate cybersecurity threats. This approach turns raw data from multiple different sources into useful intelligence, which is further used by companies to strengthen their security posture. It not only saves them from known risks but also prepares them for emerging threats.
It is safe to say that threat intelligence analysis has now become a necessity in this evolving world where digital attacks are only getting stronger.
Subscribe to our newsletter and get top Tech, Gaming & Streaming latest news, updates and amazing offers delivered directly in your inbox.