
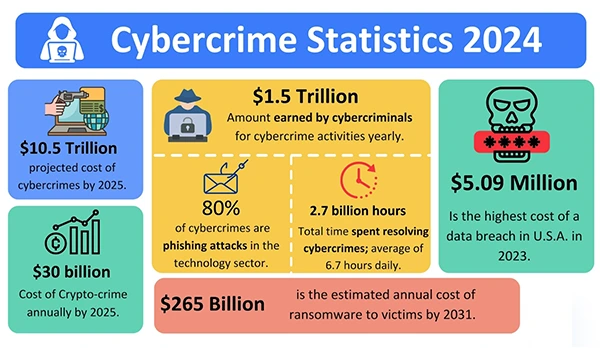
Since technology is increasingly integrating into our daily lives, cybersecurity is now more of a necessity than a luxury.
My internal conflict stems from a much younger me who used to be careless with emails, clicking on any link that seemed interesting, and instantly my whole computer was flooded with viruses.
Losing such precious documents, and dealing with those constant pop-ups was terrible for me.
It definitely taught me how to be more vigilant and secure my system in particular, and now I like to pass what I’ve learned to others.
This particular guide is suitable for all those using the Internet, and looking for some necessary practices to keep their computer and sensitive documents safe and secure.
Cybersecurity is necessary not only for me but for all those who don’t want their sensitive information to reach the wrong hands.
As a modern-day citizen, I rely heavily on the Internet for almost everything; I use various online apps to maintain sensitive information, post pictures and videos, and for financial transactions as well.
These all data are so pivotal to me and I can’t simply let any of these fall into the wrong hands, that’s the reason I prefer practicing Cybersecurity strategies to be careful of any potential cyber risks.
More than half of the corporation industry adopted technical advancements to store their customer data, financial records, and even intellectual records.
As everything is available online, the cyber attacker can easily hack the business and even ruin its reputation.
Thus, for business owners, cybersecurity is the most prominent for securing their digital assets.
In the past, large companies like Microsoft, NASA, and Sony—and even entire governments—had their systems attacked.
This rendered their websites and digital services unusable and led to great financial and reputational loss.
These few notable incidents highlight the importance of investing in robust cybersecurity measures.
Below I have shared some of the benefits I have been taking advantage of, so now you can:
Cybersecurity practices allow me to safeguard my financial assets such as bank details, my daily transactions, credit cards, etc.
Cyber hackers are more dangerous than you might think, they can simply hack your system, and destroy your reputation within seconds.
For example, in 2013, Russian hackers attacked Yahoo!, leading to 3 billion accounts being compromised.
Thus, only those who prioritize employing cybersecurity methods can reduce the chances of being attacked by hackers.
Hiring data protection measures helps you maintain the smooth operation of your business, and you can avoid downtime, losses, or potential cyber risks.
There are also some rules that state how business owners should handle the sensitive information of their customers, and cybersecurity assists in following those rules.
In this globe, every person has a separate personal digital life that they don’t want others to know about, and cybersecurity helps you maintain that.
Do You Know?
The first cyber attack is generally considered to have taken place in 1834 when two thieves accessed the French telegraph system to steal financial market information.
Every single internet user must adhere to cybersecurity practices as not only one computer but thousands of computers are being attacked in this world.
As I have so many details to store, I use various online apps to maintain them orderly.
Therefore, to keep them strongly secure and locked, I ensure the password is a mix of letters, numbers, and symbols.
VPN which stands for Virtual Private Network is designed to protect sensitive information by encrypting your data and masking your IP address.
Though the market is crowded with VPN providers, you can go with Surfshark reviews for yourself.
Daily, I communicate with so many people online, and with few, I even share so many sensitive details.
In this instance, I prefer using only encrypted platforms that ensure that no one can read them except me.
With respect to the effectiveness and profound nature of the guide so far, I encourage each one of you to adopt best practices for personal cybersecurity.
Now that we understand what measures can be taken to thwart potential cyber attacks, let’s just implement those strategies to win the battle with cyber adversaries.
Subscribe to our newsletter and get top Tech, Gaming & Streaming latest news, updates and amazing offers delivered directly in your inbox.